Spamvertised ‘Confirmed Facebook Friend Request’ Themed Emails Serve Client-Side Exploits
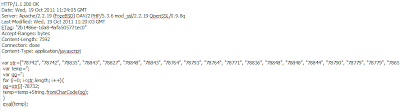
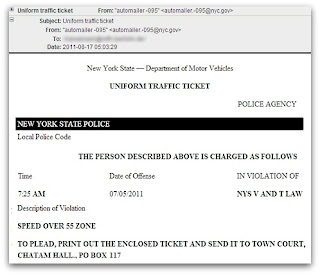
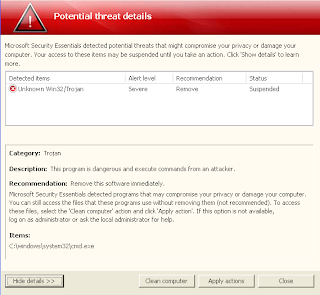
A currently circulating malicious spam campaign, entices users into thinking that they’ve received a legitimate ‘Friend Confirmation Request‘ on Facebook. In reality thought, the campaign attempts to exploit client-side vulnerabilities, CVE-2010-0188 in particular. Client-side exploits serving URL: hxxp://facebook.com.n.find-friends.lindoliveryct.net:80/news/facebook-onetime.php?dpheelxa=1l:30:1l:1g:1j&pkvby=h&rzuhhh=1h:33:1o:2v:32:1o:2v:1o:1j:1m&ycxlcvr=1f:1d:1f:1d:1f:1d:1f Detection rate for the malicious PDF: MD5: 39326c9a2572078c379eb6494dc326ab – detected by 3 out of 45 antivirus scannersRead More







![InAttack.ru Forum Official Offline Copy – [RAR] – Direct Download](https://malvertising.net/wp-content/uploads/2025/04/InAttack_Cybercrime_Forum_01-300x300.jpg)
![Hackersoft.ru Forum Official Offline Copy – [RAR] – Direct Download](https://malvertising.net/wp-content/uploads/2025/04/Forum_Hackersoft_Cybercrime_Forum_01-300x300.jpg)
![Milw0rm.com Forum Official Offline Copy – [RAR] – Direct Download](https://malvertising.net/wp-content/uploads/2025/04/Milw0rm_Cybercrime_Forum_01-300x300.jpg)
![Damagelab.org Forum Official Offline Copy – [RAR] – Direct Download](https://malvertising.net/wp-content/uploads/2025/04/Damagelab_org_Cybercrime_Forum_01-300x300.jpg)
![Mazafaka.ru Forum Official Offline Copy – [RAR] – Direct Download](https://malvertising.net/wp-content/uploads/2025/04/Mazafaka_Ru_Cybercrime_Forum_01-300x300.jpg)