Database SQL Dump of Control Booter – [SQL]
Original price was: $75.00.$70.00Current price is: $70.00.
Description
**Unearth Critical Intelligence to Combat DDoS Attacks and Disrupt Criminal Infrastructure.**
This product, the **Database SQL Dump of Control Booter – [SQL]**, provides unparalleled access to the backend infrastructure of a significant Control Booter (also known as a Stresser) service. This comprehensive SQL dump contains invaluable data that can be leveraged by cybersecurity researchers, law enforcement, and threat intelligence analysts to understand the inner workings of these malicious platforms, identify key actors, and ultimately disrupt their operations.
**What is a Control Booter (Stresser)?**
Control Booters, or Stressers, are illegal services used to launch Distributed Denial-of-Service (DDoS) attacks. These platforms allow users (often paying customers) to remotely flood target servers and networks with overwhelming traffic, rendering them unavailable to legitimate users. The disruption caused by DDoS attacks can cripple businesses, disrupt critical services, and inflict significant financial damage.
**What does this SQL Dump Offer?**
This comprehensive SQL dump provides a detailed snapshot of the Control Booter’s database structure and contents. It contains a wealth of information, including, but not limited to:
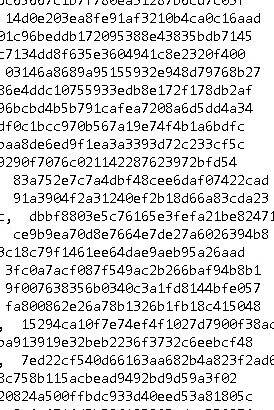
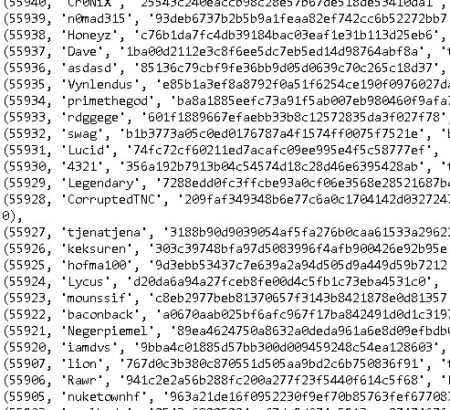
* **User Accounts:** Access to user account information, including usernames, email addresses (potentially hashed or obfuscated), registration dates, last login times, IP addresses used during registration and login, and potentially payment information. This data can be crucial for identifying and tracking individuals involved in orchestrating DDoS attacks.
* **Target Logs:** Extensive logs detailing the targets of DDoS attacks launched through the platform. This information includes target IP addresses, ports, attack types, duration of attacks, and timestamps. Analyzing these logs provides valuable insights into the platform’s usage patterns, the types of targets being attacked, and the scope of its impact.
* **Booter Infrastructure Data:** Insights into the infrastructure used by the Control Booter, including server details, botnet information (if applicable), attack vectors, and scripts utilized to launch attacks. This data can help identify the underlying infrastructure supporting the platform and potentially lead to its disruption.
* **Payment Information (Potentially):** Depending on the specific implementation of the Control Booter, the dump may contain information related to payment transactions, such as payment methods used (e.g., Bitcoin addresses, PayPal transactions), amounts paid, and transaction IDs. This data can be invaluable for tracing funds and identifying individuals profiting from the illegal service.
* **API Keys and Configurations:** Potentially exposes API keys used for connecting to other services, configurations relating to the booters infrastructure, and other sensitive information.
* **Attack Plans and Scripts:** Potential to review attack scripts, methodologies, and scheduled attacks. This can provide insight into the evolution of attack techniques and potentially predict future actions.
**Key Benefits for Researchers and Analysts:**
* **Deep Dive into DDoS Infrastructure:** Gain a comprehensive understanding of the architecture and functionality of a real-world Control Booter platform.
* **Identify Key Actors and Participants:** Uncover the identities of users, administrators, and potentially developers involved in operating the booters.
* **Track Attack Patterns and Trends:** Analyze attack logs to identify common targets, attack vectors, and trends in DDoS activity.
* **Disrupt Criminal Operations:** Utilize the intelligence gathered to dismantle Control Booter infrastructure and prevent future attacks.
* **Improve DDoS Mitigation Strategies:** Develop more effective defenses against DDoS attacks by understanding the tactics and techniques employed by Control Booter operators.
* **Enforcement and Prosecution:** Provide crucial evidence for law enforcement investigations and prosecution of individuals involved in DDoS activities.
* **Threat Intelligence Enrichment:** Integrate the data into existing threat intelligence platforms to enhance the accuracy and effectiveness of threat detection and prevention.
**Technical Specifications:**
* **Format:** SQL Dump (.sql file)
* **Database Type:** Assumed MySQL or MariaDB (compatibility testing recommended)
* **Delivery Method:** Secure Digital Download (accessible after purchase)
* **Data Size:** Varies depending on the size and activity of the Control Booter. Please check the specific file size listed on the product page.
**Disclaimer:**
* This product is intended for legitimate research and analysis purposes only.
* The information contained in this SQL dump is highly sensitive and should be handled with utmost care and security.
* It is the responsibility of the buyer to comply with all applicable laws and regulations regarding the use of this data.
* We do not endorse or condone any illegal activities.
* Due to the nature of the data, we cannot guarantee the absolute completeness or accuracy of the information contained in the SQL dump. Data may be incomplete or have been manipulated by the owners of the Control Booter.
* This product is sold “as is” and without warranty of any kind.
**Why Choose Us?**
* **Verified Source:** We obtain our data from trusted and verified sources, ensuring the highest possible level of authenticity.
* **Expert Analysis:** Our team of cybersecurity experts carefully analyzes and curates the data to provide actionable insights.
* **Secure Delivery:** We employ robust security measures to protect the confidentiality and integrity of the data during delivery.
* **Competitive Pricing:** We offer competitive pricing to make this valuable intelligence accessible to a wide range of organizations.
* **Ongoing Support:** We provide ongoing support to our customers to help them maximize the value of the data.
**Unlock the secrets behind DDoS attacks and empower your organization to combat cybercrime with the Database SQL Dump of Control Booter – [SQL]. Order yours today!**
**Note:** Before purchasing, please ensure that you have the necessary technical expertise to analyze and interpret the data contained in the SQL dump. If you require assistance, we offer consulting services to help you get the most out of this valuable resource. Please contact us for details. Also, remember to always adhere to ethical guidelines and legal regulations when working with this sensitive data.

![Database SQL Dump of Control Booter - [SQL]](https://malvertising.net/wp-content/uploads/2025/04/Control_Booter_SQL_Database_Dump_01.jpg)


![InAttack.ru Forum Official Offline Copy – [RAR] – Direct Download](https://malvertising.net/wp-content/uploads/2025/04/InAttack_Cybercrime_Forum_01-300x300.jpg)
![Hackersoft.ru Forum Official Offline Copy – [RAR] – Direct Download](https://malvertising.net/wp-content/uploads/2025/04/Forum_Hackersoft_Cybercrime_Forum_01-300x300.jpg)
![Milw0rm.com Forum Official Offline Copy – [RAR] – Direct Download](https://malvertising.net/wp-content/uploads/2025/04/Milw0rm_Cybercrime_Forum_01-300x300.jpg)
![Damagelab.org Forum Official Offline Copy – [RAR] – Direct Download](https://malvertising.net/wp-content/uploads/2025/04/Damagelab_org_Cybercrime_Forum_01-300x300.jpg)
![Mazafaka.ru Forum Official Offline Copy – [RAR] – Direct Download](https://malvertising.net/wp-content/uploads/2025/04/Mazafaka_Ru_Cybercrime_Forum_01-300x300.jpg)
Reviews
There are no reviews yet.