Database SQL Dump of Hazard Booter – [SQL]
Original price was: $75.00.$70.00Current price is: $70.00.
Description
**Unlock Unprecedented Insights into DDoS-for-Hire Operations with the Complete Hazard Booter Database Dump**
Gain exclusive access to a critical piece of cybercrime infrastructure intelligence: the complete database SQL dump from the notorious “Hazard Booter” DDoS-for-hire (Stresser/Booter) service. This deliverable provides an unfiltered, comprehensive snapshot of the operational heart of a platform responsible for facilitating numerous Distributed Denial of Service attacks across the internet.
For cybersecurity researchers, threat intelligence analysts, law enforcement agencies, and infrastructure defenders, this SQL database dump represents a unique and invaluable resource. It allows for an in-depth, ground-truth analysis of how such illicit services operate, manage users, orchestrate attacks, and handle their internal logistics.
**What is Hazard Booter?**
Hazard Booter was identified as a significant player in the DDoS-for-hire ecosystem. These platforms provide users, often with minimal technical skill, the ability to launch powerful DDoS attacks against specified targets for a fee. Understanding the inner workings of services like Hazard Booter is crucial for developing effective mitigation strategies, tracking threat actors, and comprehending the evolving landscape of cybercrime tools.
**What You Receive:**
This product consists of a single, comprehensive `.sql` file containing the complete database schema and data dump captured from the Hazard Booter platform during its operational phase. This raw data allows you to reconstruct the service’s database environment (using compatible SQL database systems like MySQL, MariaDB, PostgreSQL, etc., depending on the original format – *verification recommended*) for detailed, offline analysis.
**Potential Intelligence & Research Value:**
Analyzing this database dump can yield critical insights across multiple domains:
1. **Operational Infrastructure & Architecture:**
* **Database Schema Analysis:** Dissect the table structures, relationships, and data types used. Understand how the service organized its information regarding users, attacks, payments, servers, and configurations.
* **Technology Stack Clues:** Infer aspects of the backend technologies and frameworks employed by the service operators based on database design choices.
2. **User Base & Activity Analysis:**
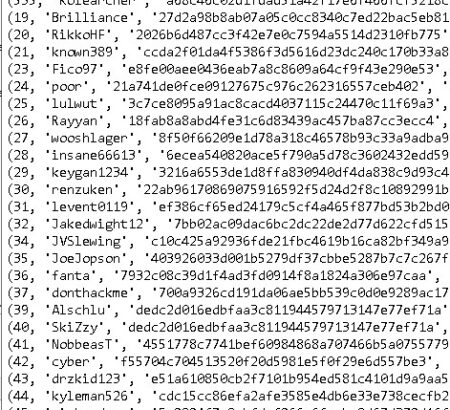
* **User Registration Data:** Examine user account details (usernames, potentially associated emails, registration timestamps, last login IPs – *Handle PII responsibly*). Identify user activity levels, registration patterns, and potential geographic concentrations.
* **User Roles & Permissions:** Understand if different user tiers or administrative roles existed within the platform.
* **API Key Usage:** Identify if the service offered an API for automated attack launching and analyze associated usage patterns.
3. **Attack Vector & Methodology Analysis:**
* **Attack Logs:** Access detailed records of launched attacks, potentially including target IP addresses/domains, ports, attack durations, selected attack methods (e.g., UDP flood, TCP SYN, Amplification methods like NTP, DNS, SSDP), attack concurrency limits, and timestamps.
* **Method Popularity:** Determine which DDoS attack vectors were most frequently offered and utilized by the platform’s users.
* **Attack Intensity & Scale:** Analyze data related to attack power (e.g., Gbps, PPS if recorded) and duration trends.
4. **Victimology & Targeting Patterns:**
* **Target Identification:** Identify the IP addresses, domain names, and potentially the types of services/organizations most frequently targeted by Hazard Booter users.
* **Targeting Trends:** Uncover patterns in victim selection over time or based on user segments. Analyze potential campaigns against specific industries or regions.
5. **Economic & Payment Insights:**
* **Subscription Plans & Pricing:** Analyze different membership tiers, their associated costs, attack capabilities, and durations.
* **Payment Methods:** Identify the payment gateways or cryptocurrency addresses (if stored) used for processing user payments. (*Note: Full transaction details may or may not be present*).
* **Revenue Analysis:** Potentially estimate the service’s revenue generation based on user subscription data and payment records.
6. **Potential Attribution & Linkages:**
* **Operator Clues:** Database configurations, comments within the schema, or specific data entries might contain inadvertent clues about the operators.
* **Correlations:** Cross-reference user identifiers (usernames, emails, IPs – *Use ethically*) with other known breaches or threat intelligence databases to potentially link actors across different platforms or activities.
**Data Structure Highlights (Potential Tables – Actual structure may vary):**
* `users`: User account information, registration details, status.
* `attacks` / `logs`: Records of initiated DDoS attacks, targets, methods, durations.
* `plans` / `subscriptions`: Details of available service tiers and user subscriptions.
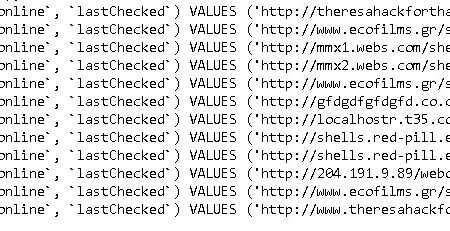
* `payments` / `transactions`: Records of payments made by users.
* `servers` / `nodes`: Information on the backend infrastructure used to launch attacks (attack servers).
* `targets`: Potentially stored target lists or presets.
* `news` / `announcements`: Platform updates or messages to users.
* `settings`: Internal configuration parameters of the booter service.
**Format & Delivery:**
* **Format:** Standard `.sql` file.
* **Compatibility:** Designed to be imported into common relational database management systems (e.g., MySQL, MariaDB, PostgreSQL). Ensure you have the appropriate environment set up.
* **Delivery:** Secure digital download link provided upon successful purchase confirmation. The file may be compressed (e.g., .zip, .gz, .rar) for efficient transfer.
**Target Audience:**
* Threat Intelligence Analysts & Teams
* Cybersecurity Researchers (Academic & Commercial)
* Malware Analysts & Reverse Engineers
* Law Enforcement Agencies (Cybercrime Units)
* National CERTs / CSIRTs
* Security Vendors (developing detection/mitigation solutions)
* Incident Response Teams
**Use Cases:**
* In-depth research into the DDoS-for-hire economy.
* Understanding threat actor TTPs (Tactics, Techniques, and Procedures).
* Developing network-based detection signatures (IDS/IPS).
* Enhancing threat intelligence platforms with ground-truth data.
* Training data for security analysis tools or machine learning models.
* Supporting investigative efforts (within legal and ethical boundaries).
* Academic studies on cybercrime ecosystems.
**Ethical Considerations & Disclaimer:**
* **Legitimate Use Only:** This database dump is provided strictly for legitimate research, cybersecurity defense, threat intelligence analysis, and law enforcement purposes.
* **Potential PII:** This dataset may contain Personally Identifiable Information (PII) related to the users (and potentially operators) of the Hazard Booter service, as well as target information. The buyer assumes **full responsibility** for handling this data ethically, securely, and in strict compliance with all applicable local, national, and international laws and regulations, including data privacy laws (e.g., GDPR, CCPA).
* **No Malicious Use:** Any use of this data for initiating attacks, harassment, extortion, or any other illegal or unethical activity is strictly prohibited.
* **No Warranty:** This data is provided “as-is.” While sourced diligently, we do not guarantee the completeness, accuracy, or integrity of every data point within the dump. The nature of illicit services means data may be incomplete, obfuscated, or contain errors.
* **Liability:** The seller assumes no liability for the buyer’s use or misuse of this data. By purchasing this product, you agree to these terms and acknowledge your responsibility for lawful and ethical data handling.
**Acquire this critical intelligence asset today and gain an unparalleled understanding of the operational mechanics behind a real-world DDoS-for-Hire service. Add the Hazard Booter SQL Database Dump to your research arsenal.**

![Database SQL Dump of Hazard Booter - [SQL]](https://malvertising.net/wp-content/uploads/2025/04/Hazard_Booter_SQL_Database_Dump_01.jpg)



![InAttack.ru Forum Official Offline Copy – [RAR] – Direct Download](https://malvertising.net/wp-content/uploads/2025/04/InAttack_Cybercrime_Forum_01-300x300.jpg)
![Hackersoft.ru Forum Official Offline Copy – [RAR] – Direct Download](https://malvertising.net/wp-content/uploads/2025/04/Forum_Hackersoft_Cybercrime_Forum_01-300x300.jpg)
![Milw0rm.com Forum Official Offline Copy – [RAR] – Direct Download](https://malvertising.net/wp-content/uploads/2025/04/Milw0rm_Cybercrime_Forum_01-300x300.jpg)
![Damagelab.org Forum Official Offline Copy – [RAR] – Direct Download](https://malvertising.net/wp-content/uploads/2025/04/Damagelab_org_Cybercrime_Forum_01-300x300.jpg)
![Mazafaka.ru Forum Official Offline Copy – [RAR] – Direct Download](https://malvertising.net/wp-content/uploads/2025/04/Mazafaka_Ru_Cybercrime_Forum_01-300x300.jpg)
Reviews
There are no reviews yet.