Database SQL Dump of Random Booter – [SQL]
Original price was: $75.00.$70.00Current price is: $70.00.
Description
The **Random Booter SQL Dump** offers a unique opportunity to peer into the architecture and functionality of a randomly selected booter/stresser service. This comprehensive SQL dump provides a diverse range of data points, offering valuable insights into the DDoS-for-hire ecosystem, even without knowing the specific identity of the platform. This product is perfect for cybersecurity researchers, threat intelligence analysts, and educators looking to broaden their understanding of these malicious services.
**Why a “Random Booter SQL Dump”?**
While knowing the specific identity of a booter (like Jay’s Booter or Hazard Stresser) is beneficial, there’s significant value in analyzing a *representative* sample. This “Random Booter SQL Dump” provides:
* **General Insights:** Even without a specific name, you can learn about common database structures, user management practices, attack logging methodologies, and payment processing techniques employed by booter services.
* **Anonymity for Research:** Studying a random platform allows researchers to focus on the *patterns* and *techniques* used, without the pressure to tie findings to a specific, named entity.
* **Cost-Effectiveness:** Offering a lower price point compared to dumps associated with specific, notorious booters, making this data accessible to a wider audience.
* **Diverse Data:** By analyzing multiple random dumps, you can identify commonalities and variations across different booter services, gaining a more holistic view of the DDoS-for-hire landscape.
**What You Might Find Inside (Data Varies by Platform):**
Because this is a “Random Booter,” we cannot guarantee specific data points. However, expect to find data related to the following (with varying degrees of completeness and accuracy):
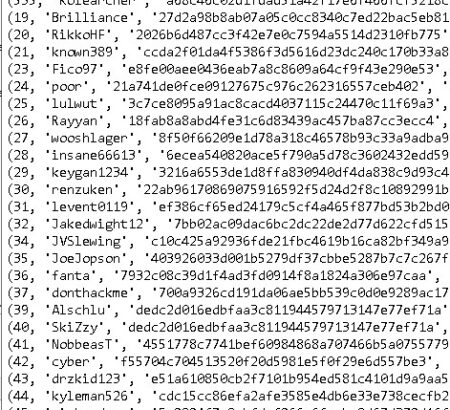
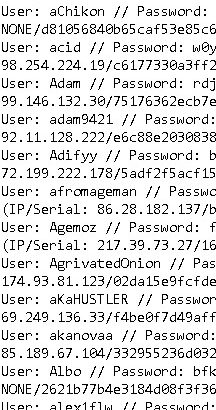
* **User Account Information:** Usernames, email addresses (potentially hashed or obfuscated), registration dates, last login times, IP addresses used during registration/login, user roles (e.g., administrator, user, reseller), and potentially security questions.
* **DDoS Attack Logs:** Target IP addresses/domain names, port numbers, attack types (e.g., UDP flood, SYN flood, HTTP flood), attack duration, timestamps, and the username of the attacking user.
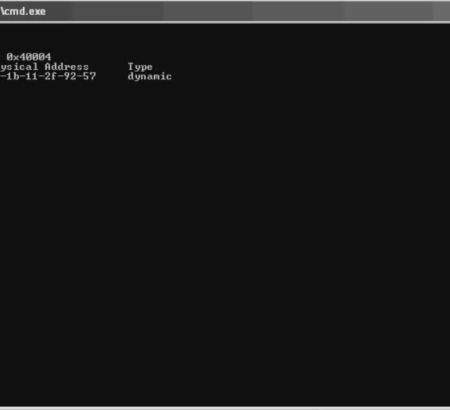
* **Booter Infrastructure Details:** Server IP addresses, configurations, botnet information (if applicable), attack scripts, control panel information, and potentially API keys for integrated services.
* **Payment Records:** Payment methods used (e.g., Bitcoin addresses, PayPal transactions, cryptocurrency exchanges), amounts paid, transaction IDs, timestamps, and associated user identifiers.
* **Pricing Structures:** Information on the various pricing tiers offered, subscription durations, and user subscription statuses.
* **Support Communications:** Records of support tickets, communication logs between users and administrators, offering insights into user issues, vulnerabilities, and internal operations.
* **Affiliate Program Data (If Applicable):** Data related to affiliate IDs, referral links, and commission payouts.
**Benefits for Cybersecurity Professionals and Educators:**
* **General Understanding of Booter Operations:** Gain insight into the typical database structure, functionalities, and user management practices common in booter services.
* **Attack Pattern Analysis:** Study attack logs to identify common targets, preferred attack vectors, and trends in DDoS activity.
* **Infrastructure Familiarization:** Understand the underlying infrastructure used by booter services.
* **Malware Analysis Insights:** Examine attack scripts and methods to understand the techniques used to execute DDoS attacks.
* **Educational Resource:** Perfect for use in cybersecurity training programs and academic research.
* **Threat Intelligence Enrichment:** General findings can be integrated into existing threat intelligence platforms to improve threat detection and prevention.
* **Cost-Effective Research:** Offers a lower-cost alternative to analyzing SQL dumps from specific, high-profile booter services.
**Technical Specifications:**
* **Format:** SQL Dump (.sql file)
* **Database Type:** Assumed MySQL or MariaDB (compatibility testing *strongly* recommended)
* **Delivery Method:** Secure Digital Download (accessible after purchase)
* **Data Size:** Varies depending on the size and activity of the specific booter. Please check the file size listed on the product page for the specific dump you’re purchasing.
**Important Disclaimers:**
* **Data Variability:** The contents of each “Random Booter SQL Dump” will vary significantly. There is *no guarantee* of specific data points.
* **”As Is” Basis:** This product is sold “as is” and without warranty of any kind.
* **Ethical and Legal Use Only:** This product is intended for legitimate research, analysis, and educational purposes only. You must comply with all applicable laws and regulations regarding the use of this data. We do not endorse or condone any illegal activities.
* **Sensitive Data Handling:** Handle the data with care, implementing appropriate access controls and security measures.
* **Technical Expertise Required:** Analyzing and interpreting this data requires technical expertise in database administration and cybersecurity principles.
* **No Identification Guarantee:** We cannot and do not guarantee the identification of the specific booter platform.
**Why Choose Us?**
* **Anonymized Source:** We ensure the source booter platform is anonymized to protect the privacy of individuals who may be inadvertently exposed.
* **Expert Data Extraction:** We employ secure methods for extracting and delivering the SQL dump.
* **Cost-Effective Learning:** We offer a valuable learning resource at an accessible price point.
**Expand your understanding of the DDoS-for-hire landscape. Order the Random Booter SQL Dump today!**
**Remember to use this information responsibly, ethically, and in compliance with all applicable laws and regulations. While the source is anonymized, responsible handling of potentially sensitive information is paramount.** This product is intended for research and educational purposes, not for engaging in any illegal activities.

![Database SQL Dump of Random Booter - [SQL]](https://malvertising.net/wp-content/uploads/2025/04/Random_Booter_SQL_Database_Dump_01.jpg)


![InAttack.ru Forum Official Offline Copy – [RAR] – Direct Download](https://malvertising.net/wp-content/uploads/2025/04/InAttack_Cybercrime_Forum_01-300x300.jpg)
![Hackersoft.ru Forum Official Offline Copy – [RAR] – Direct Download](https://malvertising.net/wp-content/uploads/2025/04/Forum_Hackersoft_Cybercrime_Forum_01-300x300.jpg)
![Milw0rm.com Forum Official Offline Copy – [RAR] – Direct Download](https://malvertising.net/wp-content/uploads/2025/04/Milw0rm_Cybercrime_Forum_01-300x300.jpg)
![Damagelab.org Forum Official Offline Copy – [RAR] – Direct Download](https://malvertising.net/wp-content/uploads/2025/04/Damagelab_org_Cybercrime_Forum_01-300x300.jpg)
![Mazafaka.ru Forum Official Offline Copy – [RAR] – Direct Download](https://malvertising.net/wp-content/uploads/2025/04/Mazafaka_Ru_Cybercrime_Forum_01-300x300.jpg)
Reviews
There are no reviews yet.