Database SQL Dump of Total Booter – [SQL]
Original price was: $75.00.$70.00Current price is: $70.00.
Description
## Database SQL Dump of Total Booter – [SQL]: Unveil the Complete Landscape of a Booter/Stresser Service
**Delve into the Core of DDoS-for-Hire: A Comprehensive SQL Dump for Unprecedented Cybercrime Research.**
The **Database SQL Dump of Total Booter – [SQL]** offers an unparalleled deep dive into the operational heart of a significant booter/stresser service, known as “Total Booter.” This meticulously extracted SQL dump provides a holistic view of the platform’s infrastructure, user base, attack history, and internal mechanisms, empowering cybersecurity researchers, law enforcement agencies, and threat intelligence analysts to effectively combat DDoS attacks and dismantle criminal networks.
**Understanding Total Booter: A Key Player in the DDoS-for-Hire Ecosystem**
Booter services, or stressers, like Total Booter, operate as illicit platforms facilitating Distributed Denial-of-Service (DDoS) attacks. These services enable individuals, often with limited technical skills, to launch crippling attacks against target servers and networks, causing widespread disruption, financial losses, and reputational damage. Understanding the inner workings of these services is crucial for effective cybersecurity defense and law enforcement efforts.
**What Makes This SQL Dump “Total”?**
Unlike partial dumps, this product aims to provide the *most comprehensive* database snapshot available for Total Booter, maximizing the potential for in-depth analysis. While complete data retrieval is never guaranteed, this dump strives to include all accessible tables and fields, offering a fuller picture than typical data breaches.
**Inside the Dump: A Goldmine of Cybercrime Intelligence**
This SQL dump is a treasure trove of information, potentially including (but not limited to – actual data varies based on the platform’s architecture and security measures):
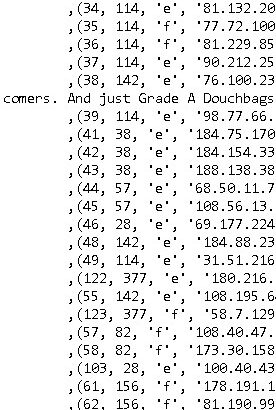
* **Comprehensive User Account Data:** This includes usernames, email addresses (potentially hashed or obfuscated), registration timestamps, last login details, associated IP addresses, user roles (e.g., admin, user, reseller), and potentially security questions/answers. This data is crucial for identifying and tracking perpetrators involved in ordering and launching DDoS attacks.
* **Detailed Attack Logs & Target Information:** A comprehensive record of DDoS attacks launched via Total Booter, including target IP addresses/domain names, port numbers, attack vectors (e.g., UDP flood, SYN flood, HTTP flood), attack duration, timestamps, and potentially the user who initiated the attack. Analyzing this data reveals attack patterns, targeted industries, and the scale of the service’s impact.
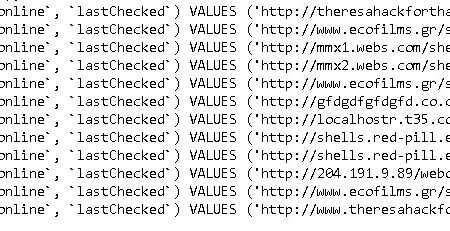
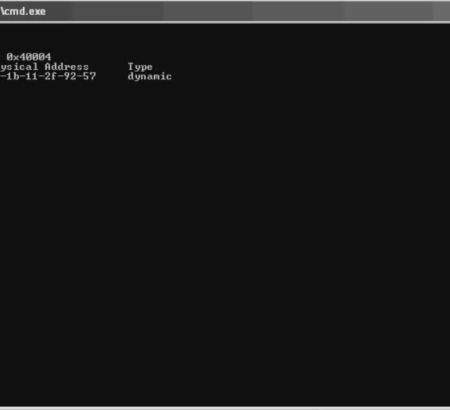
* **Booter Infrastructure & Server Details:** Insights into the underlying infrastructure powering Total Booter, including server IP addresses, configurations, botnet information (if applicable), attack methods and scripts, and potentially control panel details. This data can facilitate the identification and takedown of the platform’s infrastructure.
* **Payment Transaction Records:** Transaction details, including payment methods used (e.g., Bitcoin addresses, PayPal transactions, cryptocurrency exchanges), amounts paid, transaction IDs, timestamps, and potentially user identifiers associated with payments. This data is essential for tracing illicit funds and identifying individuals profiting from the booter service.
* **Pricing Plans and Subscription Data:** Information on the various pricing tiers offered by Total Booter, subscription durations, and user subscription status. This data provides insight into the business model and revenue generation of the platform.
* **API Keys and Integration Details:** Exposed API keys used for connecting to other services (e.g., payment gateways, botnet providers), configuration settings, and other sensitive information related to the platform’s internal workings.
* **Support Tickets & User Communication:** Records of support tickets submitted by users, communication logs, and potentially internal discussions among Total Booter administrators, offering valuable insights into user issues, vulnerabilities, and internal operations.
* **Affiliate Programs (if applicable):** Data related to any affiliate programs used by Total Booter to recruit new users, including affiliate IDs, referral links, and commission payouts.
**Benefits for Cybercrime Research and Mitigation:**
* **Complete Understanding of a Booter Service:** Gain an in-depth understanding of the architecture, functionality, and operational procedures of Total Booter.
* **Identification of Key Actors:** Uncover the identities of users, administrators, developers, and other individuals involved in the booter service.
* **DDoS Attack Pattern Analysis:** Analyze attack logs to identify common targets, preferred attack vectors, and trends in DDoS activity.
* **Infrastructure Takedown:** Utilize infrastructure data to identify and disrupt the servers and networks powering Total Booter.
* **Financial Disruption:** Trace illicit funds and identify individuals profiting from the booter service to aid in financial investigations and asset forfeiture.
* **Enhanced Threat Intelligence:** Integrate the data into existing threat intelligence platforms to improve threat detection and prevention capabilities.
* **Law Enforcement & Prosecution:** Provide crucial evidence for law enforcement investigations and prosecution of individuals involved in DDoS attacks and related cybercrimes.
* **Improved DDoS Mitigation Strategies:** Develop more effective defenses against DDoS attacks by understanding the tactics and techniques employed by Total Booter users.
**Technical Specifications:**
* **Format:** SQL Dump (.sql file)
* **Database Type:** Assumed MySQL or MariaDB (compatibility testing highly recommended)
* **Delivery Method:** Secure Digital Download (accessible after purchase)
* **Data Size:** Varies significantly depending on the size and activity of Total Booter. Refer to the specific file size listed on the product page for accurate information.
**Important Disclaimers and Considerations:**
* **Ethical Use and Legality:** This product is intended for legitimate research, analysis, and law enforcement purposes only. It is crucial to comply with all applicable laws and regulations regarding the use of this data. We do not endorse or condone any illegal activities.
* **Data Completeness and Accuracy:** While we strive to provide the *most comprehensive* dump possible, we cannot guarantee the absolute completeness or accuracy of the data. Information may be missing, incomplete, manipulated, or outdated.
* **Handling Sensitive Data:** The data contained in this SQL dump is highly sensitive and requires careful handling and security measures. Ensure proper access controls and data protection protocols are in place.
* **”As Is” Basis:** This product is sold “as is” and without warranty of any kind.
* **Technical Expertise Required:** Analyzing and interpreting the data contained in the SQL dump requires significant technical expertise.
**Why Choose Us?**
* **Source Verification:** We prioritize obtaining data from reliable and verified sources to ensure authenticity.
* **Expert Extraction & Curation:** Our team of cybersecurity professionals meticulously extracts and analyzes the data to provide valuable insights.
* **Secure Delivery:** We employ robust security measures to protect the confidentiality and integrity of the data during delivery.
* **Competitive Pricing:** We offer competitive pricing to make this critical intelligence accessible to a wide range of organizations.
* **Consulting Services (Optional):** We provide optional consulting services to assist you with analyzing and interpreting the data, maximizing its value. Contact us for details.
**Uncover the complete picture of a booter service and strengthen your defenses against DDoS attacks. Order the Database SQL Dump of Total Booter – [SQL] today!**
**Remember to exercise caution, adhere to ethical guidelines, and comply with all applicable laws when working with this sensitive data.**

![Database SQL Dump of Total Booter - [SQL]](https://malvertising.net/wp-content/uploads/2025/04/Total_Booter_SQL_Database_Dump_01.jpg)


![InAttack.ru Forum Official Offline Copy – [RAR] – Direct Download](https://malvertising.net/wp-content/uploads/2025/04/InAttack_Cybercrime_Forum_01-300x300.jpg)
![Hackersoft.ru Forum Official Offline Copy – [RAR] – Direct Download](https://malvertising.net/wp-content/uploads/2025/04/Forum_Hackersoft_Cybercrime_Forum_01-300x300.jpg)
![Milw0rm.com Forum Official Offline Copy – [RAR] – Direct Download](https://malvertising.net/wp-content/uploads/2025/04/Milw0rm_Cybercrime_Forum_01-300x300.jpg)
![Damagelab.org Forum Official Offline Copy – [RAR] – Direct Download](https://malvertising.net/wp-content/uploads/2025/04/Damagelab_org_Cybercrime_Forum_01-300x300.jpg)
![Mazafaka.ru Forum Official Offline Copy – [RAR] – Direct Download](https://malvertising.net/wp-content/uploads/2025/04/Mazafaka_Ru_Cybercrime_Forum_01-300x300.jpg)
Reviews
There are no reviews yet.